Agenda
Zero Trust and Microsoft Endpoint Manager Overview
Introduction to cloud-native Windows endpoints
Building your first cloud-native Windows endpoint
Setting up the environment
Managing the device configurations, applications and updates
Building a cloud-native Windows endpoint with Autopilot
Looking forward and Resources
Microsoft Zero Trust
Zero Trust is a security approach that never trusts and always verifies identities, devices, and services. Microsoft has adopted and implemented Zero Trust to protect corporate and customer data. The implementation centers on strong user identity, device health verification, validation of app health, and least-privilege access to resources and services. Microsoft uses Conditional Access as the main policy engine for Zero Trust, which can block or give limited access to resources based on various signals or conditions¹. Microsoft also offers services to help organizations assess their security posture and achieve Zero Trust alignment.
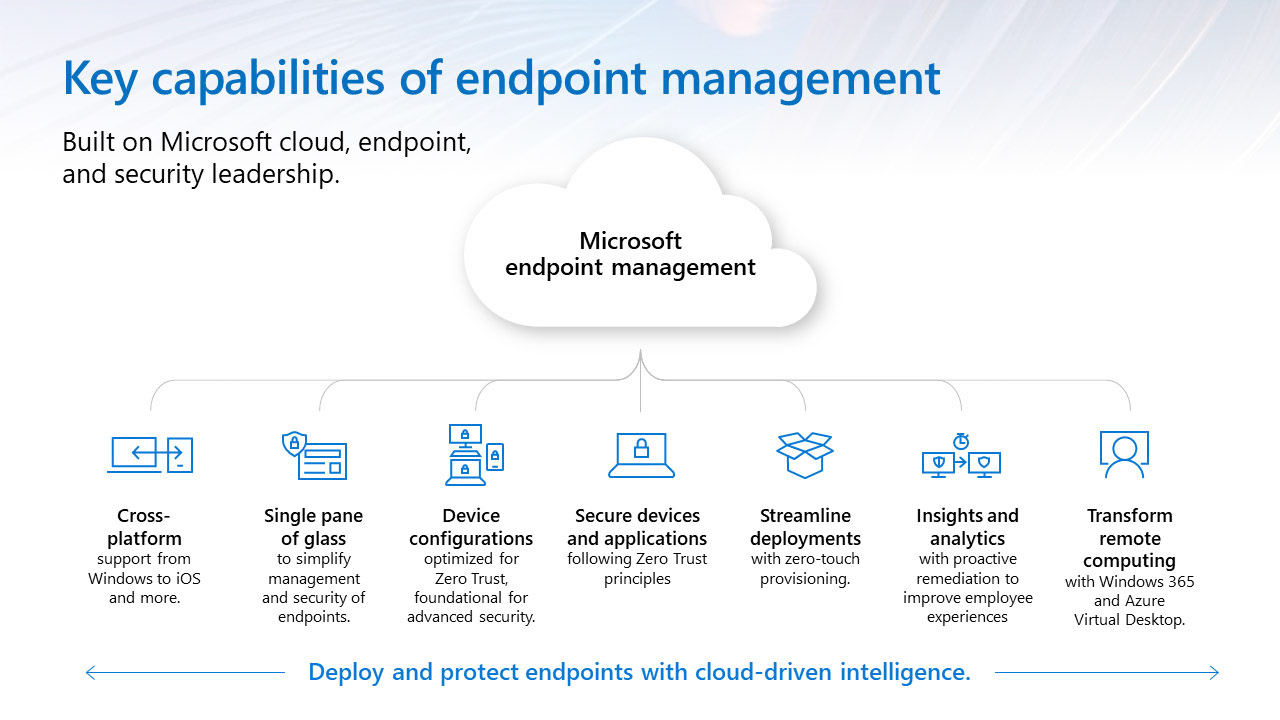
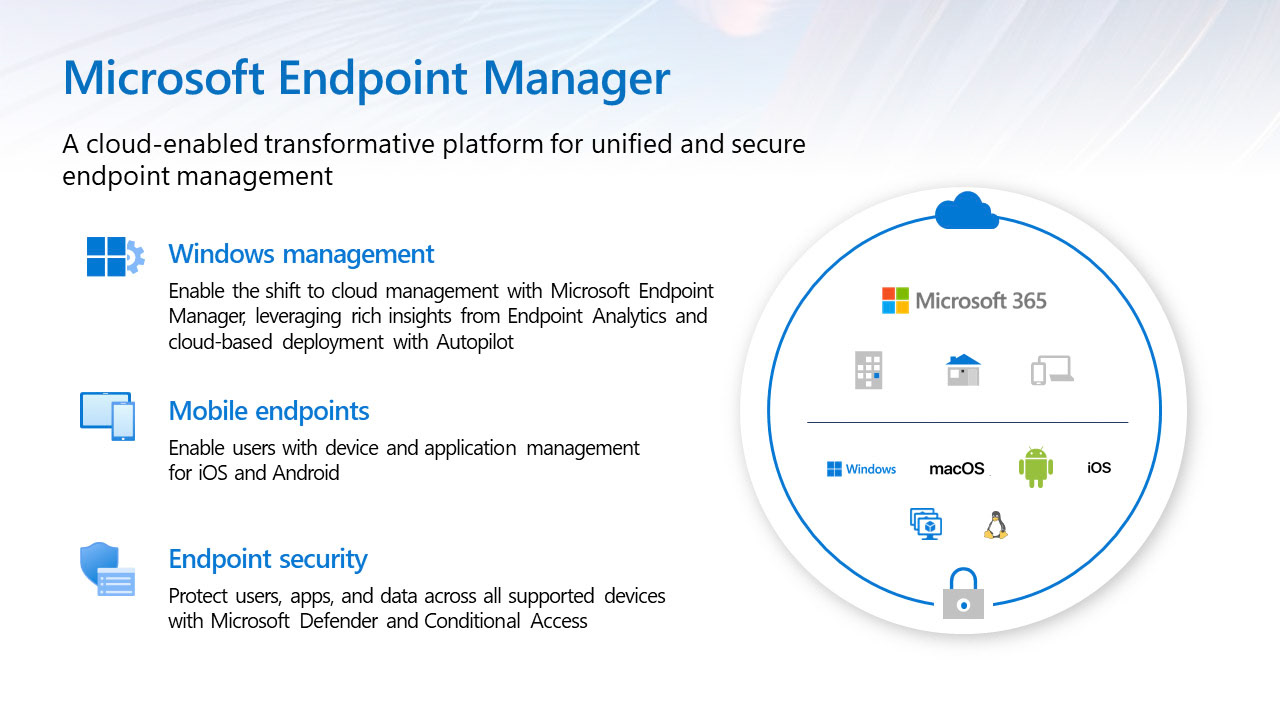
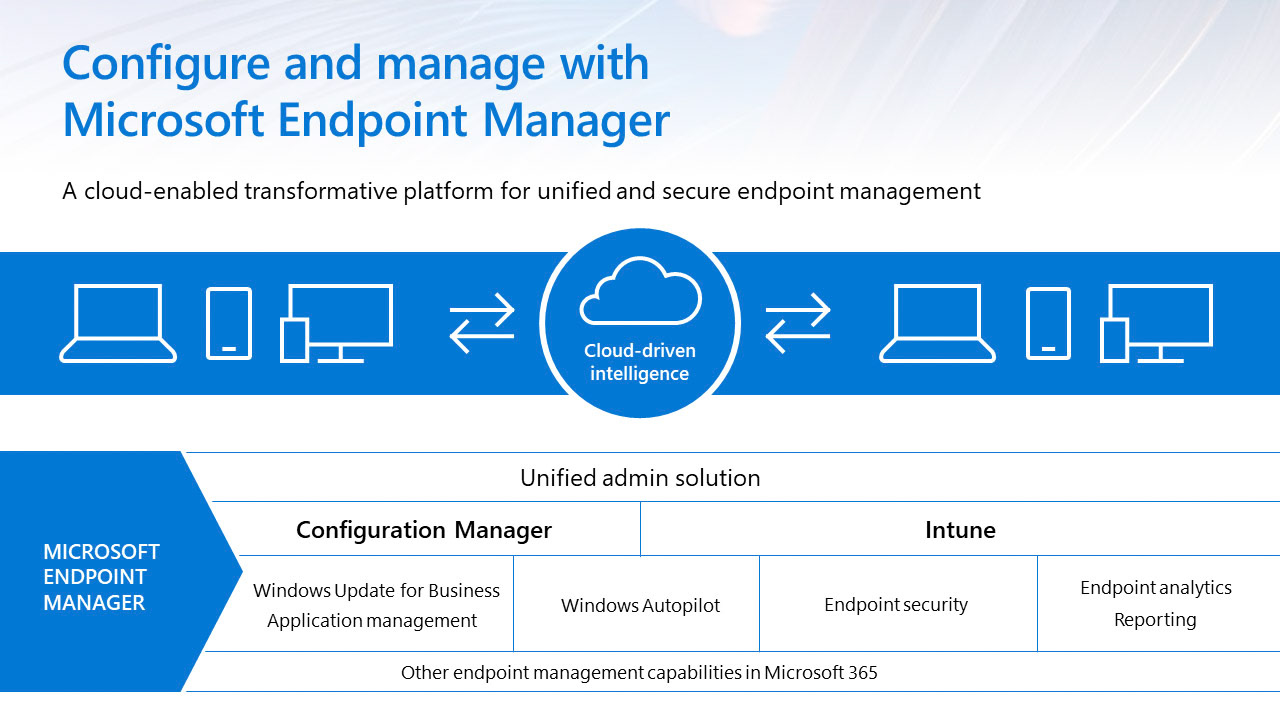
Microsoft Endpoint Manager Overview
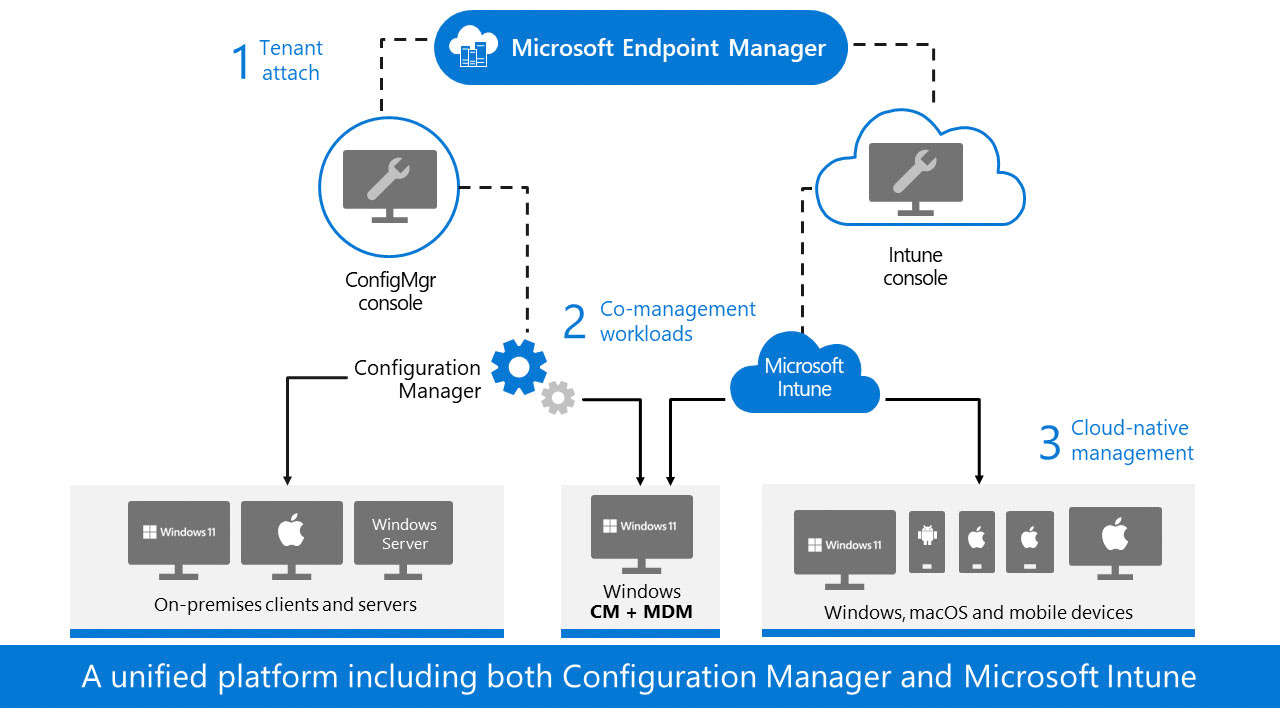
Microsoft Endpoint Manager is a solution that combines different services and tools to manage and protect devices, apps, and data in the cloud and on-premises. It includes Microsoft Intune, Configuration Manager, Desktop Analytics, co-management, and Windows Autopilot. It supports a diverse range of endpoints, including mobile, desktop, virtual, embedded, and server devices. Microsoft Endpoint Manager helps deliver the modern workplace and the best productivity experience for end users. Depending on the needs of the organization, Microsoft Endpoint Manager can be used to manage only cloud-based endpoints, only on-premises endpoints, or a combination of both with cloud attach.
Some benefits of Microsoft Endpoint Manager include increased security and productivity, flexibility, maximized investment, centralized endpoint management by attaching on-premises devices to the cloud.
Device Identity & Authentication
Hybrid Azure AD Join and Azure AD Join are two different ways to connect devices to Azure AD. Hybrid Azure AD Join allows users to access both cloud and on-premises resources, simplifies Windows device deployments, and enables greater single-sign on capabilities. When a device is both Azure AD Joined and hybrid Azure AD joined, the hybrid Azure AD join takes precedence for authentication and Conditional Access evaluation. A hybrid joined computer is joined to both the local AD and Azure AD, but the AD join is primary because the device uses AD authentication. Azure AD Join is the best starting point for users starting out with Intune.
Windows Cloud Endpoint (Intune) Overview and Benefits
Microsoft Intune is a cloud-based service that provides mobile device management (MDM) and mobile application management (MAM) capabilities. It allows you to manage Windows devices and apps from a single console. Some benefits of using Intune to manage Windows devices include
Simplified device management: You can manage all your devices from a single console, including Windows PCs, Macs, iOS devices, Android devices, and more.
Increased security: You can enforce policies to protect your data and devices, such as requiring strong passwords or encrypting data on devices.
Improved productivity: You can deploy apps and updates to devices remotely, which can save time and reduce downtime.
Better compliance: You can ensure that your devices are compliant with your organization's policies and regulations.

Windows 11
benefits
Windows 11 also sets a new benchmark for performance and security, which will help businesses and educational institutions optimize for productivity. Windows 11 can help shield employees and students against an ever-changing roster of cyberthreats. Provided below is a link to the windows 11 compatibility checker.
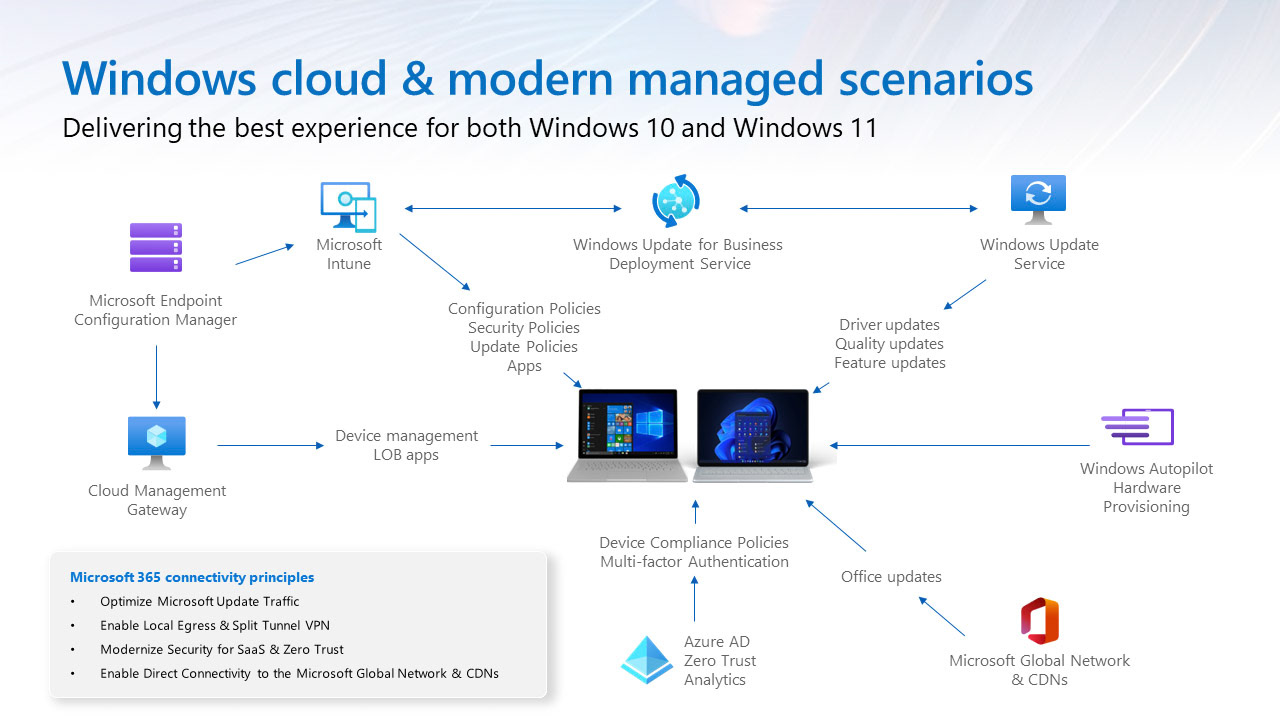
Steps to Configuring a Cloud Native Endpoint
Use the ordered phases in this guide, which build on each other to help you prepare your cloud-native Windows endpoint configuration.
Before You Begin
admin centers & logins
Security Considerations
Recommendations for ensuring you have the access you need
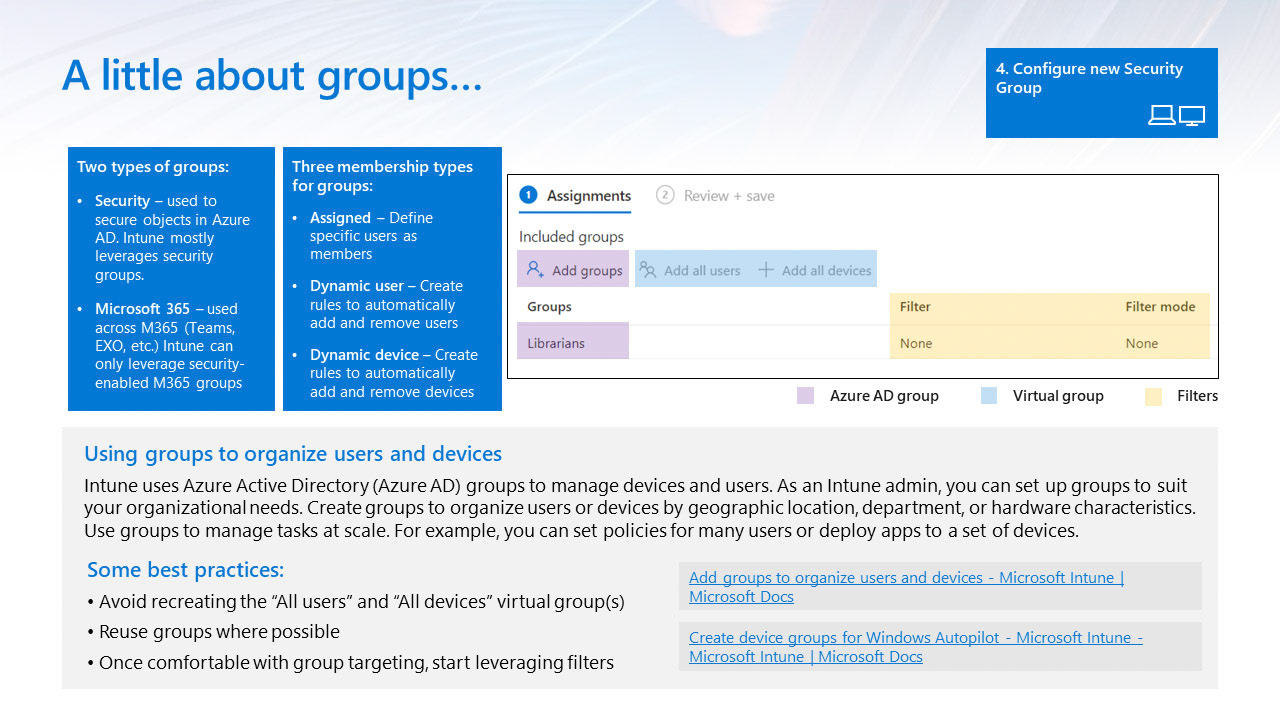
Role-based access control (RBAC)
Helps you manage who has access to your organization's resources and what they can do with those resources. By assigning roles to your Intune users, you can limit what they can see and change. Each role has a set of permissions that determine what users with that role can access and change within your organization.
To create, edit, or assign roles, your account must have one of the following permissions in Azure AD:
Global Administrator
Intune Administrator
The following portion of the guide is meant to help prepare your environment
Set up your environment to build your first cloud-native Windows endpoint
Networking Requirements
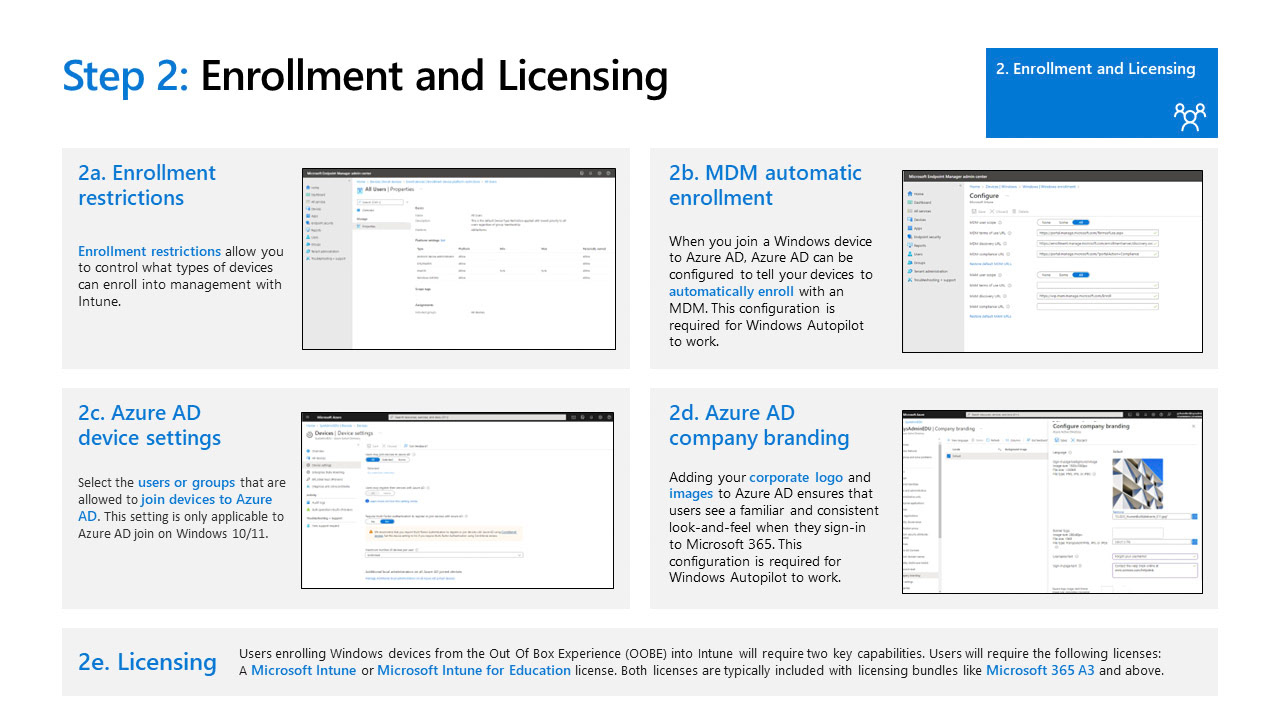
Enrollment and Licensing
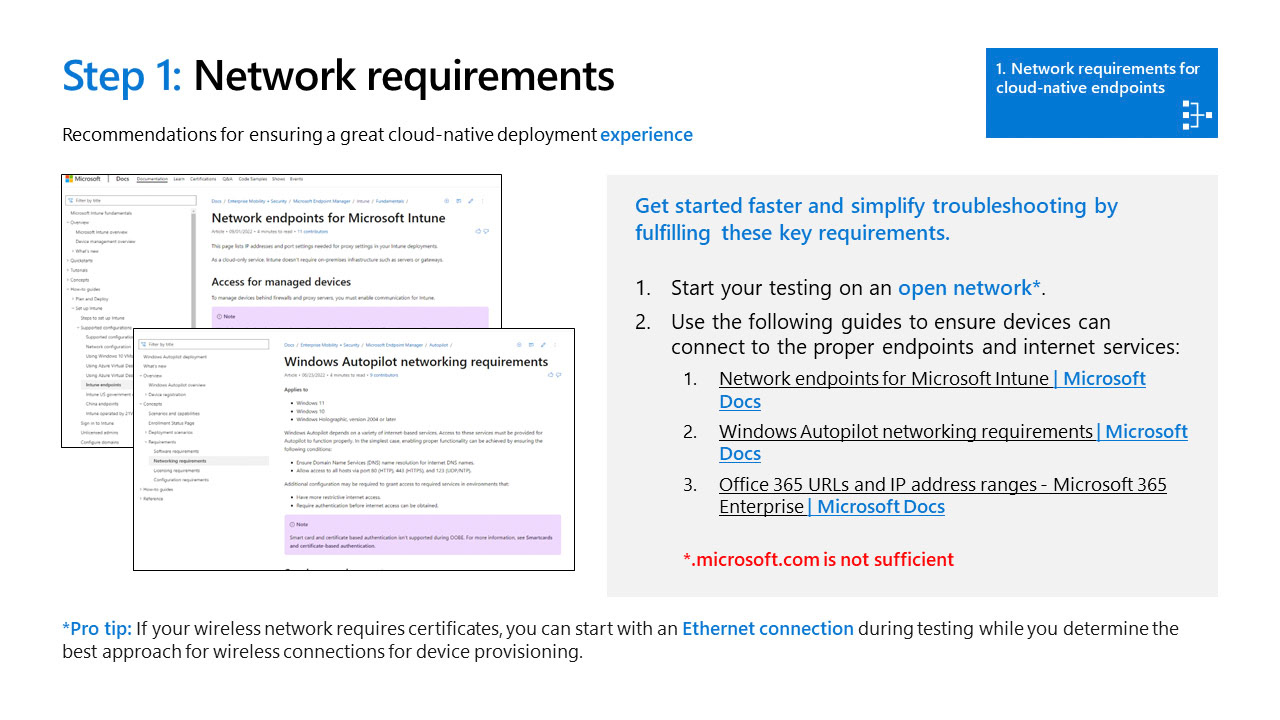
Education Networking Tips
Networking within educational institutions can have additional requirements. K-12 institutions in particular can be impacted due to the need for a filtering provider. CIPA (Child Information Protection Act (Link) requires many types of K-12 institutions to filter internet connections that students use often times it needs to operate regardless of device location. Out of network protection is extremely important.
Make sure to whitelist all Intune and M365 URL's above in your filtering provider otherwise communication issues can occur leading to device management problems.
Common Education Filtering Providers
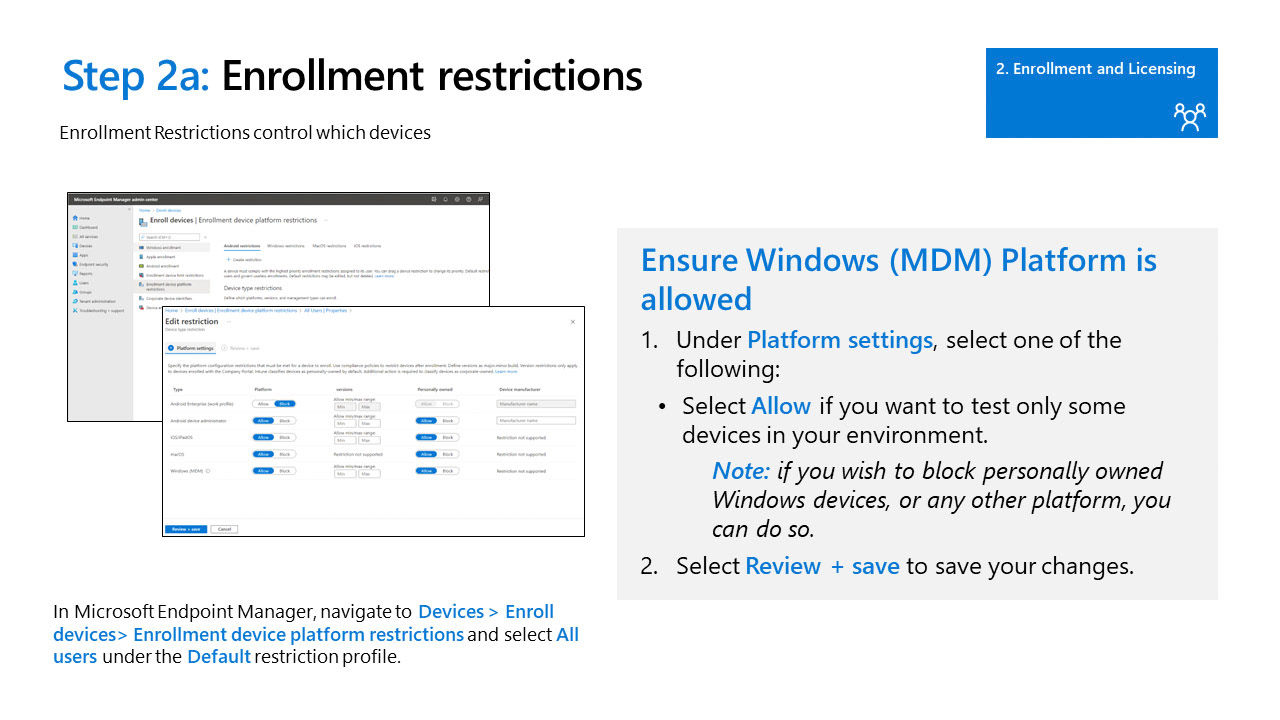
Enrollment Restrictions
(Blocking personally owned devices from Intune)
MDM Automatic Enrollment
(Blocking bring your own devices)
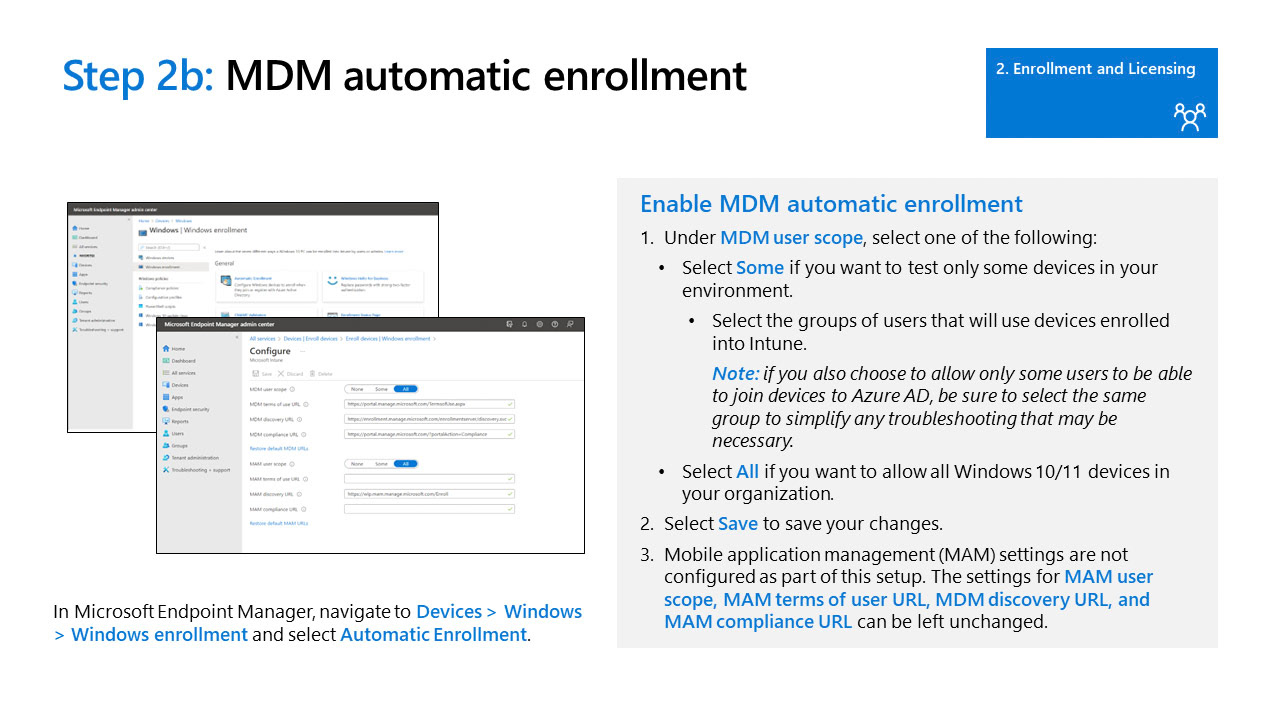
Personally Owned Devices in Education
It's important to understand that in an education setting that managing personally owned devices comes with added legal risk. If you push policies or applications to personally owned devices situations can occur where the only way, they can reset their device is to call your IT department. It's recommended to block personal enrollment in educational settings.
Bring your own device in education
It's Important to understand that bring your own device scenarios are often populated by devices that are personally owned. In an educational k-12 setting this this is often times recommended to disable in addition to personally owned devices. If you'd like to manage cell phones or other personally owned devices with Intune, you will need to enable both options.
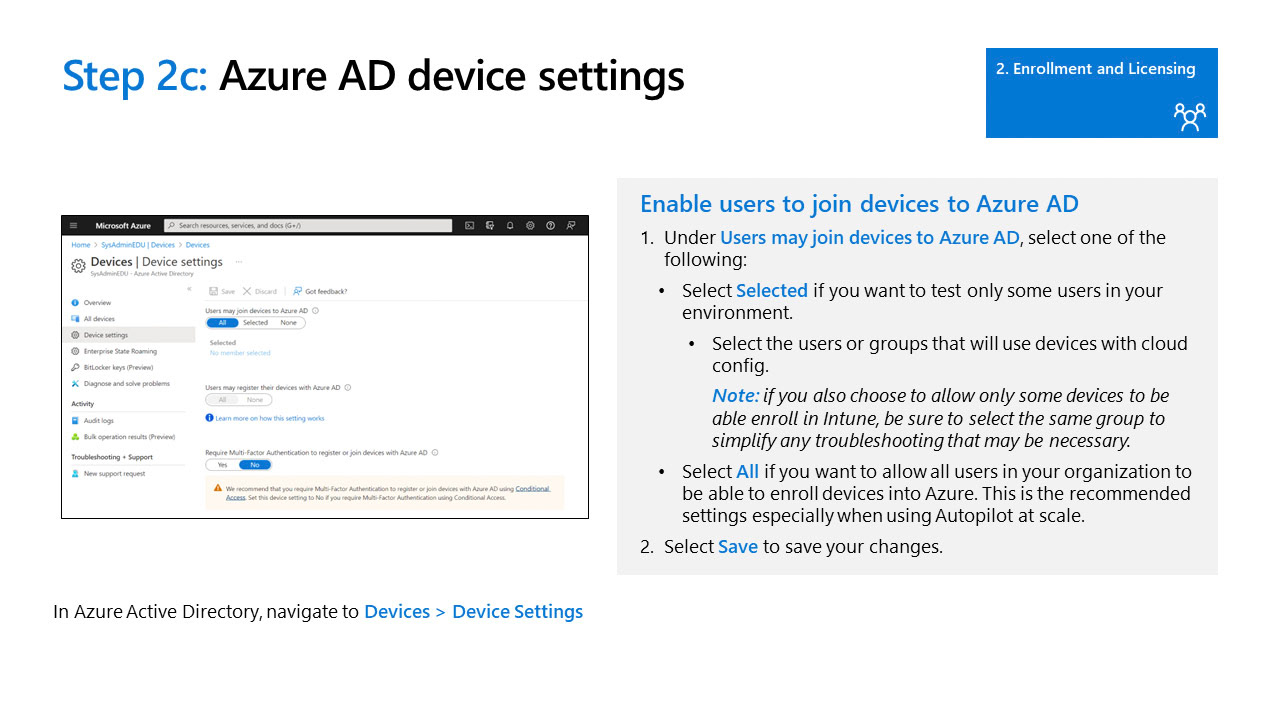
Azure active directory device setting changes
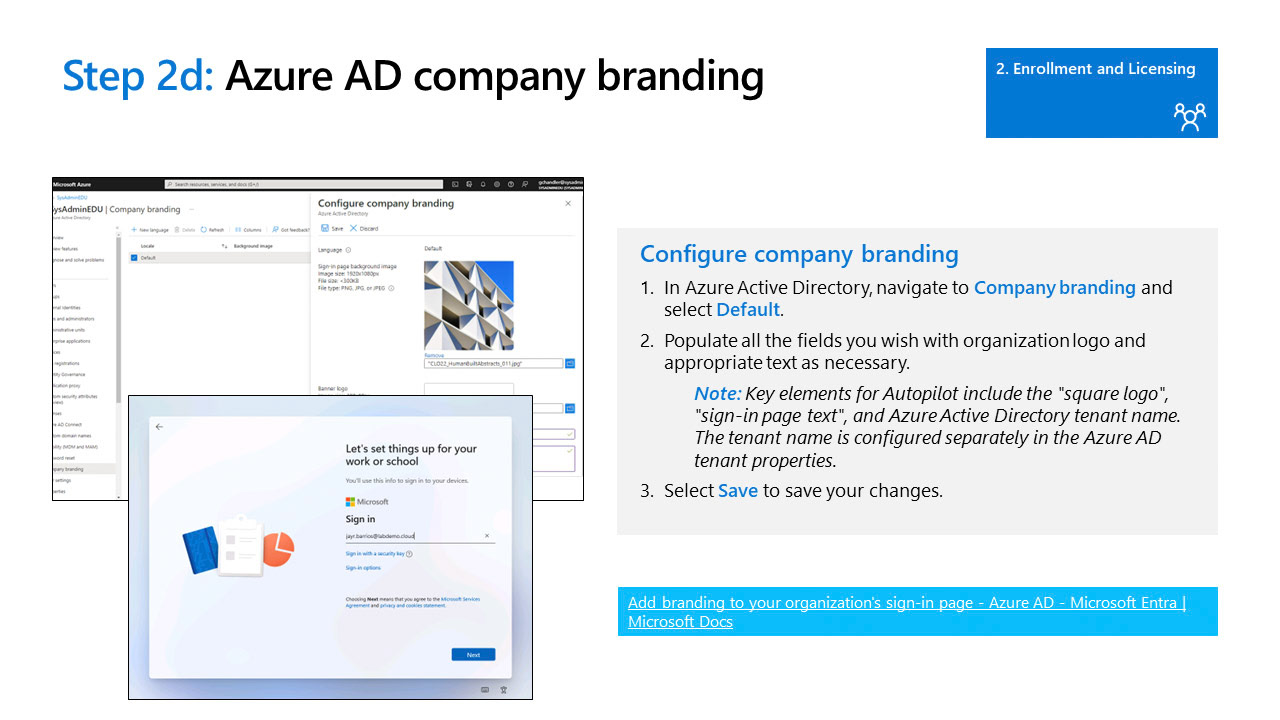
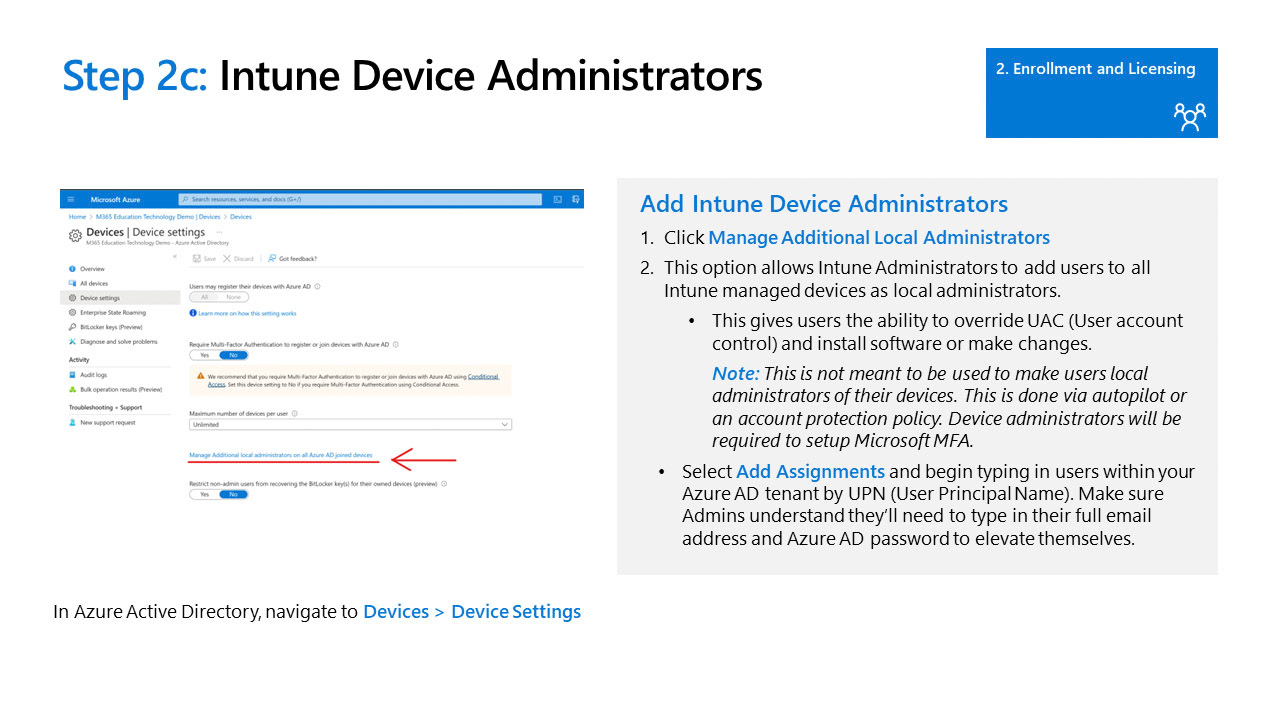
In order to better manage and support Intune devices its recommended to make some changes in the azure portal. This will include things such as device administrators, company branding, and enterprise state roaming. link to your azure portal below.
Azure AD Device Enrollment Settings
Azure & Intune Company Branding
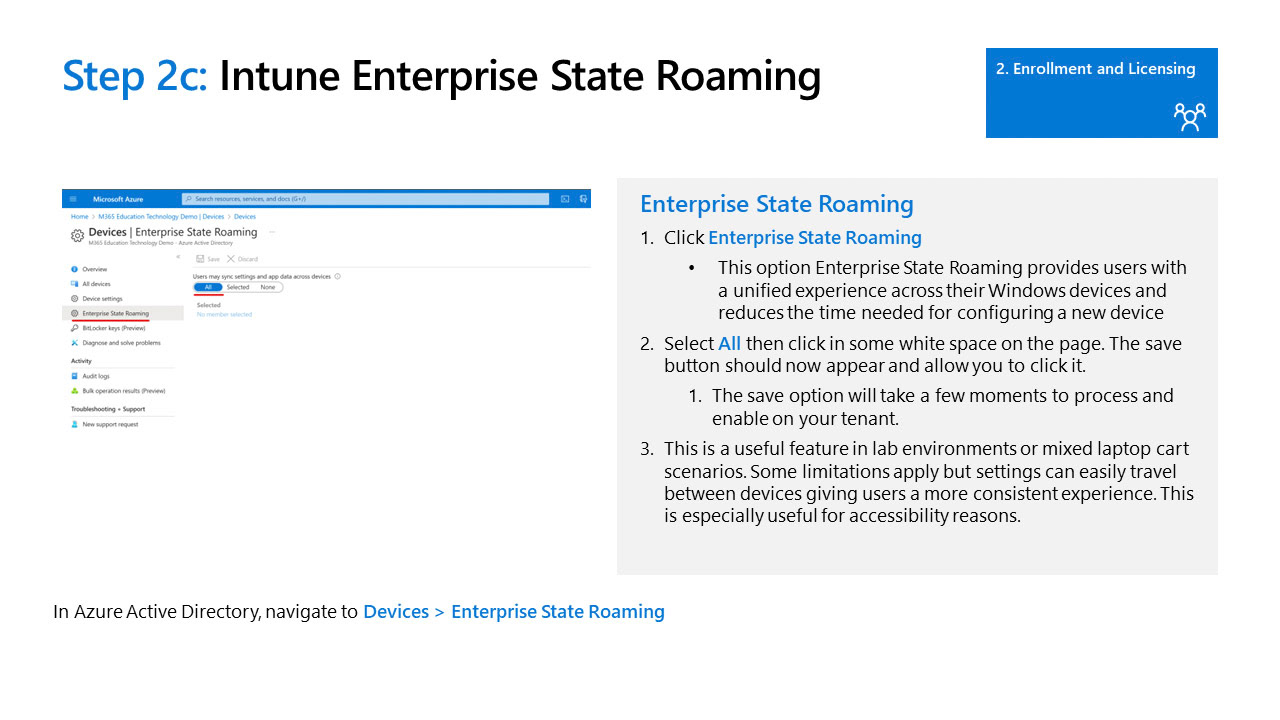
Intune Required Licensing
INtune Optional Licensing
Windows AutoPilot Overview
Windows Autopilot is a collection of technologies used to set up and pre-configure new devices, getting them ready for productive use. Windows Autopilot can be used to deploy Windows PCs or HoloLens 2 devices. When new windows 10 or 11 devices are first brought online and connected to the internet, they connect to the autopilot service to determine they are owned by an organization. using a hardware hash imported by a partner or manually imported by IT Administrators. autopilot runs through preconfigured autopilot enrollment profiles to prepare the devices for organizational use.
Autopilot Deployment steps & Considerations
Importing a test Device
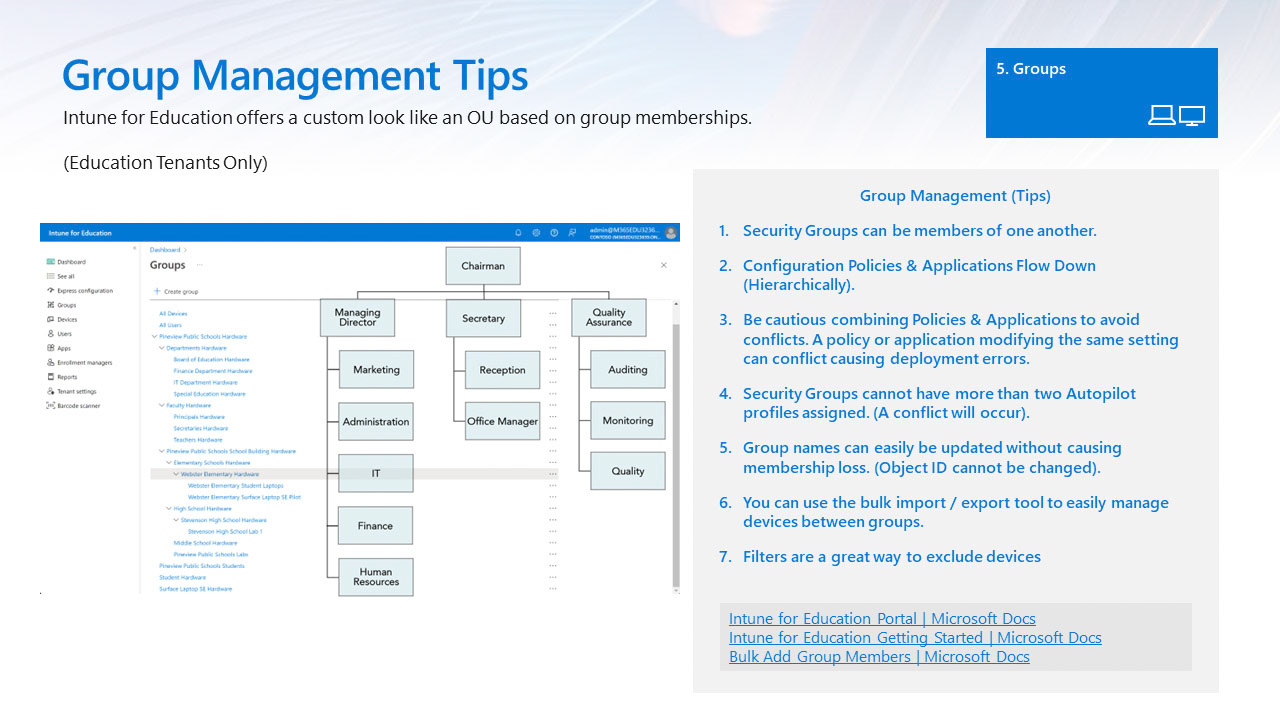
To begin testing autopilot you'll need to setup a few things so the device can properly enroll in your Intune tenant. Please view the guidance below on how to import A test device into autopilot, create groups using automation or manual assignments, Group Hierarchy in the Intune for Education Portal, how to configure the enrollment status page, and assigning an autopilot profile.
If the device was previously imaged and deployed either via system center or connected to local active directory manually please make sure to reset the device back to factory settings and delete the computer objects in those systems. If you do not it can cause issues with deploying devices with Intune and AutoPilot.
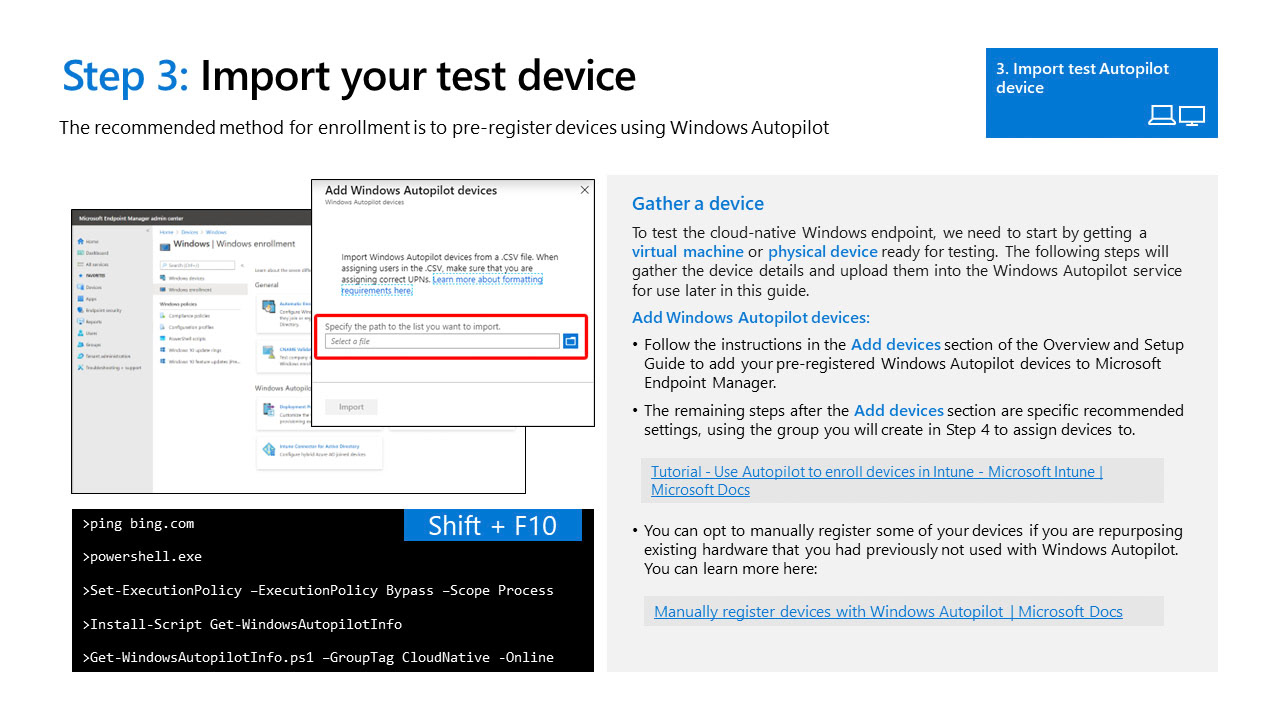
Powershell Commands
PowerShell.exe
Set-ExecutionPolicy -ExecutionPolicy Bypass -Scope Process
Install-Script Get-WindowsAUtoPilotINfo
Get-WindowsAutoPILOTInfo.ps1 -GroupTag CloudNative -Online
(You May need to Consent to Graph API)
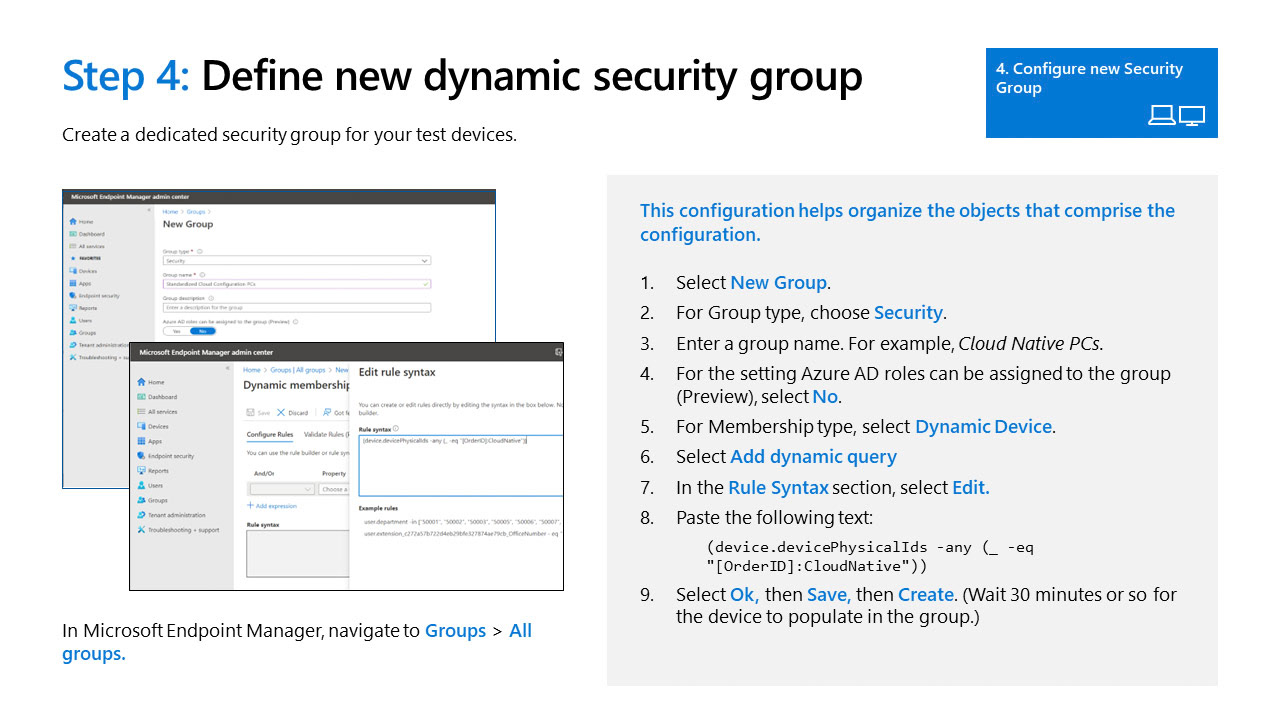
Group Rule Syntax
in the rules section select edit or click the pencil
Paste the Following Text
(device.devicePhysicalIds -any _ -eq "[OrderID]:CloudNative")
you may have multiple group tags depending on need
This can enable you to scale quickly
Using Groups and Autopilot to scale
Using automated group tagging you can scale device deployments quickly. Once the group hierarchy and dynamic group memberships are mapped customers can easily call a partner and request a purchase based on this group tag. This allows customers to separate and onboard devices quicker.
Example
200 Staff Laptops
Group Tag: STAL
500 Student Laptops
Group Tag: STUL
It's important to note that autopilot profiles can inherit down via group membership but be careful about causing conflicts. If you accidentally assign two profiles to the same group whichever profile is assigned first is the profile that will be assigned causing deployment problems.
Configure Enrollment status page
The enrollment status page is what modifies the OOBE (Out of box experience) customers see when using autopilot user enrollment profiles. this is important in education because we can use this to force install applications and make sure policies are enforced before students can access the desktop. Its particularly useful to deploy the filtering products mentioned above.
Configure AutoPilot Profiles & Assign them
Now that we've customized OOBE we need to deploy an autopilot profile to a group containing devices we've imported into the service. the autopilot profile is what will also name the device. Currently autopilot only supports naming devices 15 characters long so keep that in mind when creating your first profile. Multiple profiles will be needed if naming by buildings.
Deploying Applications with Intune
Intune supports deploying a wide variety of application types based on the supported operating system. since application installations can be performed multiple ways on windows device finding the proper deployment can take time as silent installation methods are traditionally used in education. This website also has some guides curated to assist with this process. Please feel free to use what's available below at the following link.
It's recommended to repackage all windows applications as win32 to gain access to additional features and avoid enrollment failures during autopilot setup.
Microsoft Application Repository
Microsoft has released the (New Store APp) experience in the Intune application deployment portal. This is powered by winget and the newest microsoft store changes. The current Microsoft store for education and store for business are currently being deprecated. Please do not integrate them.
Deploying M365 Applications
Microsoft has made it easier than ever to deploy the M365 applications for Enterprise / Education. The applications are natively built into the Intune console for customization and deployment however if you'd like even more customization of the office apps or to deploy device based activated versions you can utilize the portal link below to create an XML to import and deploy with Intune.
Device Configuration Profiles
Intune uses device configuration service profiles (CSP) to manage policies on the targeted windows devices. This is a modern management method and replaces the need for group policy under most circumstances. CSP profiles also use modern methods to make changes to the device making it easier to diagnose and review issues as people are migrating to Intune.
If you are testing hybrid management, first make sure to understand that in that deployment scenario group policies will always apply over csp profiles. This means if you create a policy that affects the same settings, your group policy will apply first and the csp will fail to apply causing a conflict in Intune.
Settings to Try
Feel free to try the settings below for a more optimal user experience when using windows devices. The following policies configure the edge browser and OneDrive known folder move.
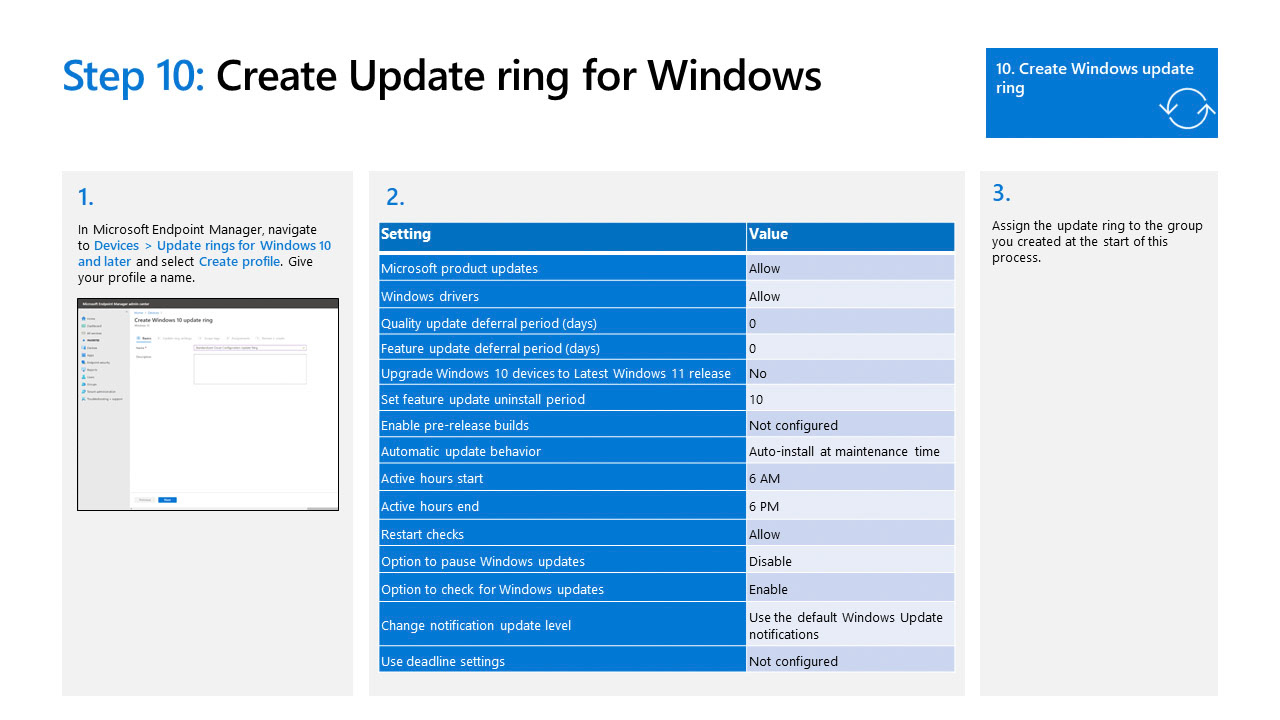
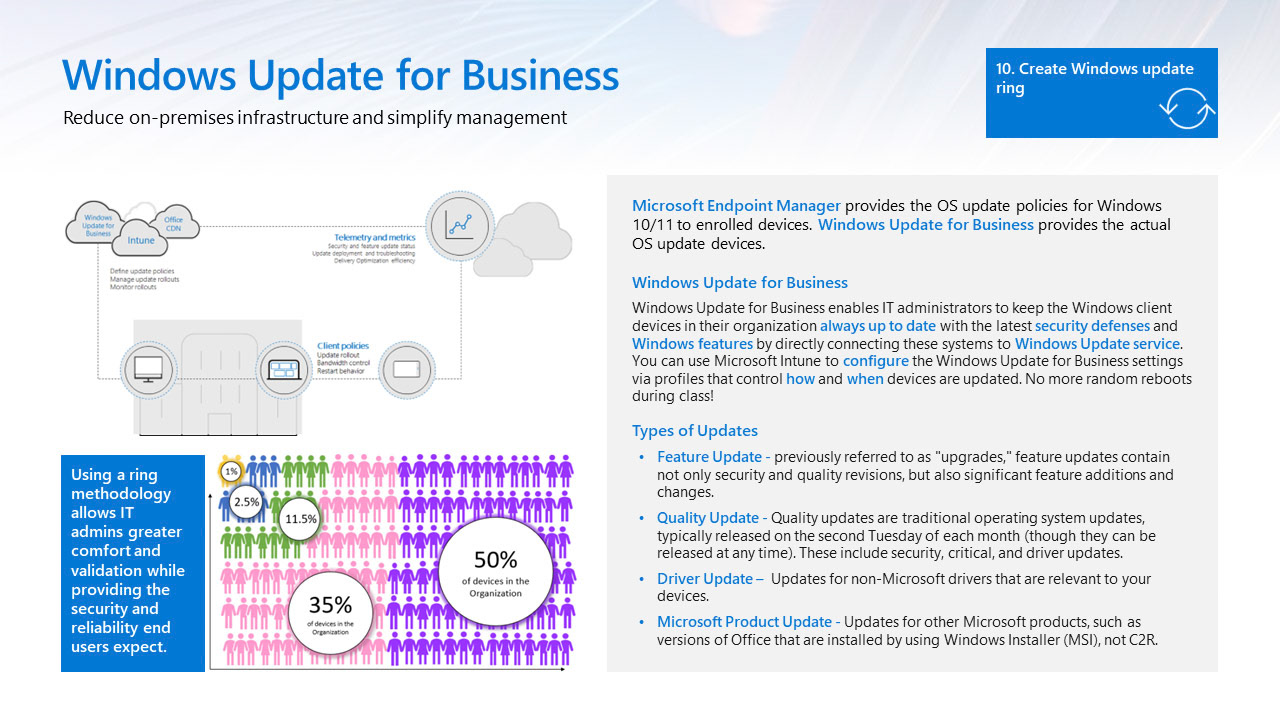
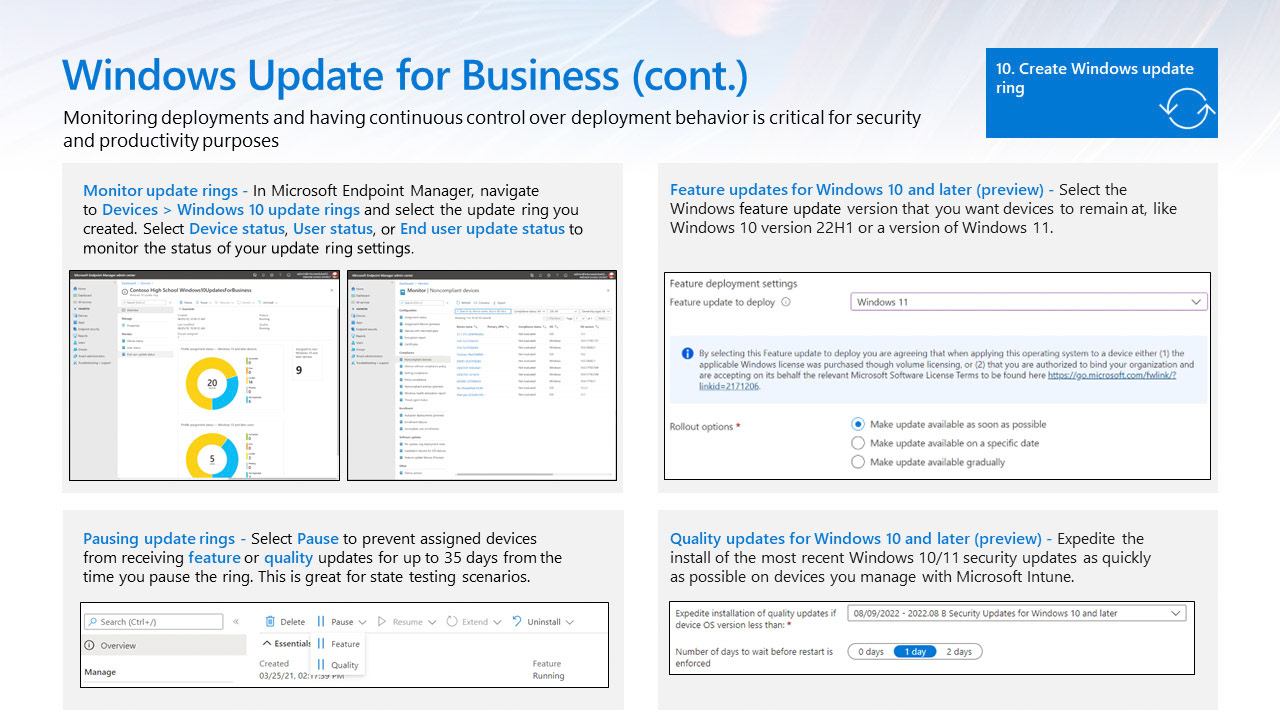
Windows update for business
Windows Update for Business (WUFB) is a collection of technologies that helps you to keep the Windows client devices in your organization always up to date with the latest security defenses and Windows features by directly connecting these systems to Windows Update service.
Here are some key benefits of using Windows Update for Business:
- Greater control over update deployment
- Greater visibility into device update health
- Provides controls to help meet your organization’s security standards
- Enables you to set automatic updates at times that work well for people in your organization
- Provides a positive update experience for people in your organization.
Testing your first device deployment
Now that you've gone through this overview feel free to test a device deployment with autopilot. A short video has been included showing the manual import process and autopilot enrollment.
Managing the device with Intune
with intune as as the device management system you have a multitude of options available to you to manage devices. Below are some of the most common uses.
Modern Management Myths and FAQ
Next Steps
Below you will find guidance on next steps during your modern management journey.
Additional Resources
Technical Resources
Community Resources
Top2k EDU Office Hours
tyler's YouTube Channel
Thankyou
We hope you found this overview of intune helpful









